Introduction
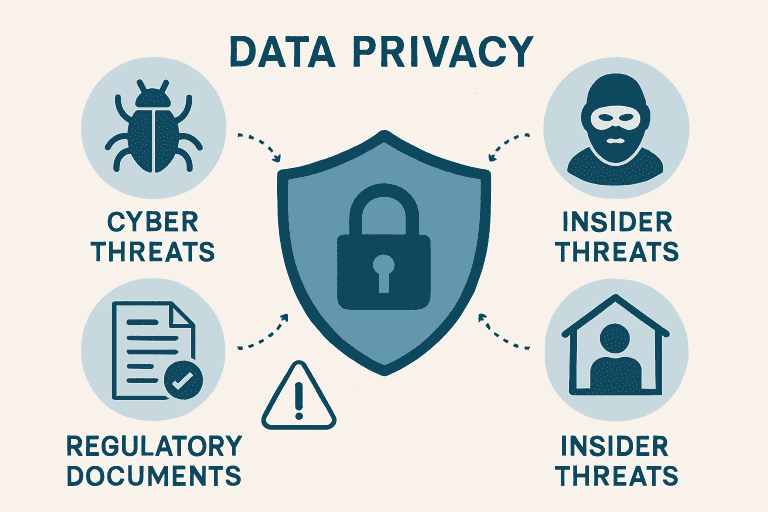
In today’s hyper-connected environment, data privacy has become a top priority, whether you’re protecting personal records or overseeing enterprise-wide information governance. With cyber threats growing more sophisticated, data breaches making headlines, and regulatory demands becoming stricter, safeguarding sensitive data is increasingly challenging and essential. Organizations seeking to strengthen their defenses must implement adaptable and robust data security frameworks that respond to evolving risks and shifting compliance expectations. For more insights on structuring effective protection strategies, visit https://www.cohesity.com/solutions/data-security/.
Staying one step ahead of malicious actors isn’t easy. Data privacy threats morph constantly, impacting everything from individual privacy to international business reputation. Organizations and users can more effectively secure their information and build trust in the digital landscape by understanding the various risks and the latest defense strategies.
Cyber Threats: The Ever-Present Danger
Cyberattacks continue to be one of the most relentless threats to data privacy in today’s hyper-connected world. With malware, ransomware, and phishing schemes becoming more sophisticated, individuals and enterprises are at constant risk. Attackers exploit weak entry points to steal sensitive information, disrupt operations, and extort victims. The financial and reputational damages are profound—global cybercrime costs are projected to exceed $9.5 trillion in 2024 alone, affecting organizations across all sectors. A single data breach can compromise proprietary information, expose customer records, and tarnish brand reputation, often resulting in legal consequences and diminished stakeholder trust. From healthcare and finance to e-commerce and education, no industry is immune. Cybersecurity strategies must now be proactive, not reactive, combining advanced tools with continuous staff training and policy enforcement. Prioritizing data privacy and cyber hygiene has never been more crucial in safeguarding long-term business stability and maintaining regulatory compliance in an evolving digital environment.
Insider Threats: The Enemy Within
External cyber threats often dominate headlines, but many significant security breaches originate within an organization. Insider threats—whether deliberate or accidental—are responsible for approximately 60% of successful data breaches. These risks can stem from disgruntled employees intentionally compromising systems, staff members misusing privileged access, or simple human errors like clicking phishing links or mishandling confidential data. The impact of these actions can be just as damaging as external attacks, leading to data loss, reputational harm, and regulatory consequences. To mitigate these risks, businesses must adopt proactive internal security measures. This includes implementing role-based access controls, monitoring user activity, enforcing strict password hygiene, and running routine access audits. Educating employees about cybersecurity best practices also plays a crucial role. Strengthening insider threat detection and response capabilities is vital for maintaining a secure digital environment and reducing the likelihood of internal vulnerabilities being exploited.
Regulatory Challenges: Navigating the Legal Landscape
The data privacy regulatory environment grows more complex each year. With the introduction of statutes such as the Washington State My Health My Data Act (effective March 2024), organizations must continually adapt to varying requirements across jurisdictions. These laws can address everything from protecting health records to handling and transferring consumer data. Compliance is more than a legal necessity—it is vital to building and maintaining customer trust in digital operations.
Emerging Technologies: Balancing Innovation and Privacy
Emerging technologies offer promise—but also considerable risk—for privacy. Artificial Intelligence (AI) models often require massive volumes of personal data for training and inference, raising questions regarding consent and transparency. Similarly, Internet of Things (IoT) devices gather data streams, increasing the risk of unauthorized surveillance or large-scale data exposures. Strong encryption, regular vulnerability scans, and privacy-by-design principles should accompany all technological innovation efforts to minimize these risks.
Proactive Strategies: Building a Robust Defense
Strengthening data defenses before an incident occurs is far more cost-effective than managing a breach aftermath. Leading organizations utilize a suite of tools and protocols, including:
- Data Encryption: Ensures that sensitive information is unreadable to unauthorized users, both in transit and at rest.
- Regular Security Audits: Identify system flaws and strengthen defenses with frequent reviews and updates.
- Access Controls: Implements strict authorization protocols based on job roles or responsibilities, limiting the risk of unnecessary exposure.
Employee Training: Cultivating a Security-Conscious Culture
Human error remains a leading cause of data breaches, accounting for over two-thirds of security incidents across industries. To combat this, employee education is vital to any successful cybersecurity strategy. Ongoing training equips staff with the skills to recognize phishing scams, avoid unsafe links, and properly manage sensitive data. A strong program reinforces secure password habits, promotes vigilance against social engineering, and outlines clear protocols for reporting suspicious activity. By embedding security awareness into daily routines, organizations foster a proactive culture that reduces risk and limits vulnerabilities. Regular simulations and updates ensure that employees stay informed as threats evolve. Building an informed workforce is one of the most cost-effective and impactful ways to strengthen overall cyber defense and prevent unnecessary cyberattack exposure.
Third-Party Risks: Ensuring Partner Compliance
Working with third-party vendors and external partners can expand operational capacity and introduce significant data privacy risks. Even if your internal cybersecurity measures are strong, a single vulnerable partner can become an easy entry point for attackers. Data breaches often occur due to weak vendor protocols, inadequate encryption, or poor access controls. Organizations must implement a comprehensive third-party risk management program to mitigate these risks. This includes thoroughly vetting all partners for regulatory compliance, security certifications, and adherence to best practices for data privacy. Ongoing audits, continuous monitoring, and clearly defined contractual obligations are critical to ensure vendors maintain proper safeguards. These proactive measures protect sensitive data, reinforce trust, reduce legal exposure, and enhance overall cybersecurity across the extended enterprise.
Future Trends: Preparing for What’s Next
The future of privacy protection will depend on continuously adapting to a rapidly transforming landscape. Anticipated trends include:
- AI-Driven Threat Detection: Revolutionary AI-powered tools can detect and neutralize threats in real-time, improving responsiveness across large datasets.
- Quantum Computing: Advances in quantum technology may challenge today’s encryption standards, urging businesses to prepare for next-generation cryptographic solutions.
- Enhanced Privacy Regulations: Governments worldwide are expected to introduce even stricter laws, requiring companies to stay nimble and proactive in compliance efforts as privacy expectations escalate.
Forward-thinking individuals and organizations are best positioned to protect sensitive data by combining strong internal policies, the latest security technology, and a persistent awareness of the changing legal and threat landscape.

 How Code Compliance Impacts Modern Construction Projects
How Code Compliance Impacts Modern Construction Projects  Smart Ways to Protect and Style Your Vehicle with Window Tinting
Smart Ways to Protect and Style Your Vehicle with Window Tinting  Sara Saffari Height: Exact CM/Feet, Real‑World Perception, and Comparisons
Sara Saffari Height: Exact CM/Feet, Real‑World Perception, and Comparisons  What to Do When Your New Car Has Issues
What to Do When Your New Car Has Issues  Top Reasons Companies Are Outsourcing Their Customer Support in 2025
Top Reasons Companies Are Outsourcing Their Customer Support in 2025  Future Trends in Voice Over IP
Future Trends in Voice Over IP  TV Off Lyrics Meaning: Themes, Context, and Why It Resonates
TV Off Lyrics Meaning: Themes, Context, and Why It Resonates  Leanne Morgan Net Worth: 2025 Earnings, Income Streams, and Career Milestones
Leanne Morgan Net Worth: 2025 Earnings, Income Streams, and Career Milestones  Why Sexual Harassment Training Is Essential for a Respectful Workplace
Why Sexual Harassment Training Is Essential for a Respectful Workplace