The hackers are at it again. Phone bugs are a handful at any point of
We live in a world connected by Android Phones to the internet. Over the years,
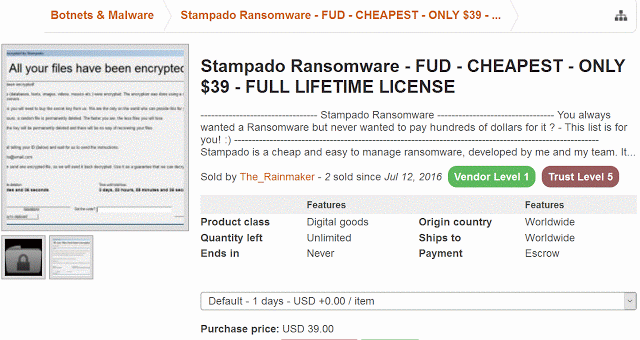
For all you Tech-Savvy geeks, there is a way to earn mindboggling millions with just
Security has become synonymous with the Smartphone in the recent past years. A number of
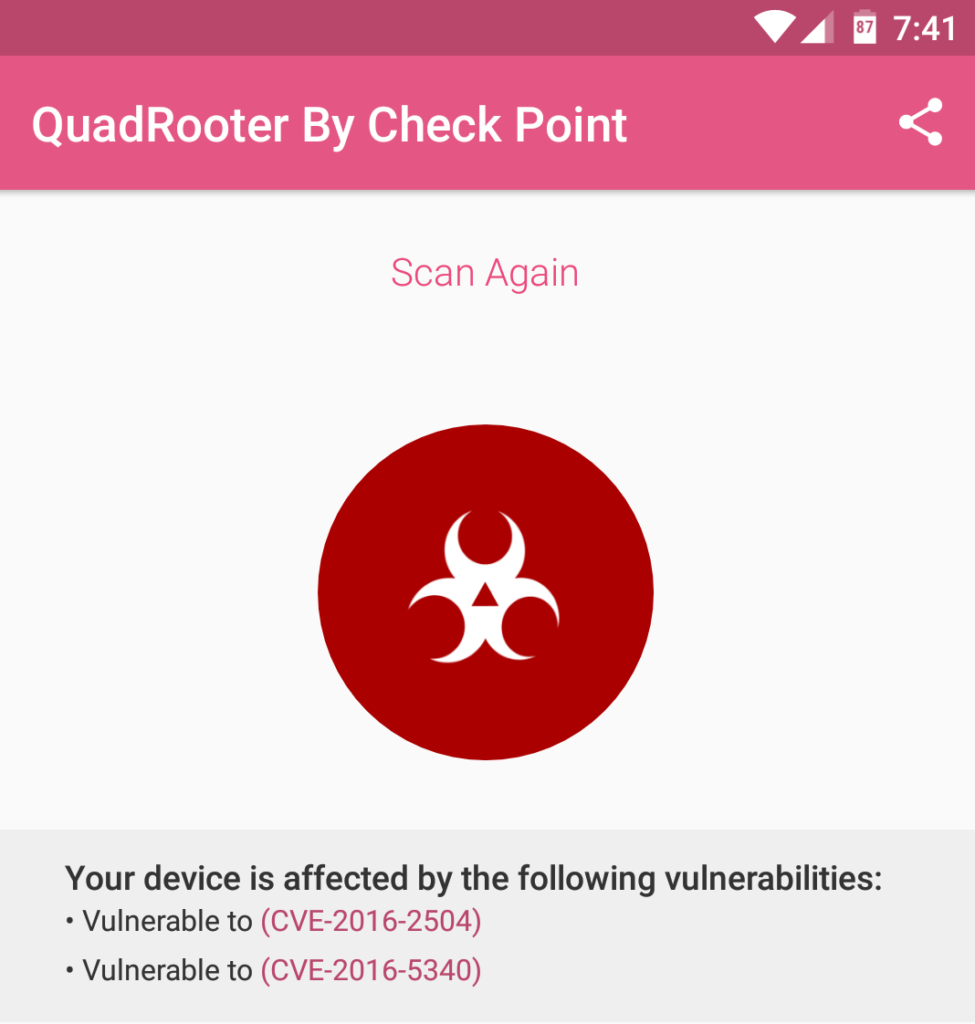
Four threats, identified recently, are showing the intensity to affect over 900 million users, using
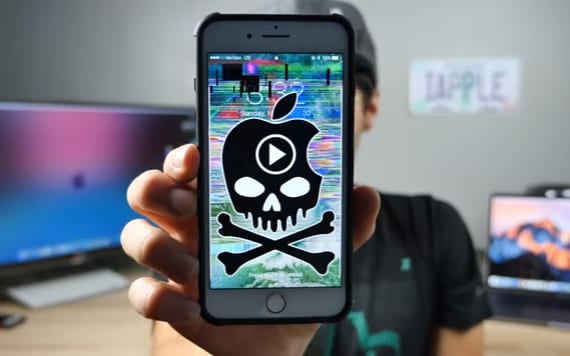
A new malware has emerged from the darkness which has the ability to take control
One of the new systems of hacking or damaging high profile computer networks is
Hackers can be simply put as the highly talented individuals who use their intelligence
Apple Mac computers are regarded as the most secured device which doesn’t get penetrated

 How SASE Solutions Empower Productive Workforces in a Digital Era
How SASE Solutions Empower Productive Workforces in a Digital Era  Excel vs PDF: Which Dominates Document Sharing in 2025? (Data-Driven Comparison)
Excel vs PDF: Which Dominates Document Sharing in 2025? (Data-Driven Comparison)  TitaniumInvest.com Money 2024: AI‑Driven Tools Outperform Traditional Banking
TitaniumInvest.com Money 2024: AI‑Driven Tools Outperform Traditional Banking  Why Your Link Building Efforts Might Fail
Why Your Link Building Efforts Might Fail  How to Request or Give Remote Control in a FaceTime Call on iPhone
How to Request or Give Remote Control in a FaceTime Call on iPhone  The Rise of Intelligent Automation in Business Operations
The Rise of Intelligent Automation in Business Operations  The Best Ideas for Designing Your Custom Printed Ring Binder
The Best Ideas for Designing Your Custom Printed Ring Binder  How Technology is Changing the Way We Play Hearts
How Technology is Changing the Way We Play Hearts  The Rise of Open Source: A Journey to Innovation and Collaboration
The Rise of Open Source: A Journey to Innovation and Collaboration